In the 1950s, the new strategic challenges engendered by the Cold War grew to be more complex than anything that generals and diplomats had seen before. They asked mathematicians for help, and game theory was developed to facilitate strategic decisions in adversarial situations. The Cold War is now over, but game theory is still used to model the adversarial situations in various sciences, and in daily trading on the markets. The problems of cyber security are also complex and adversarial. Why is game theory not a standard tool of cyber security, like it is a standard tool of economics?
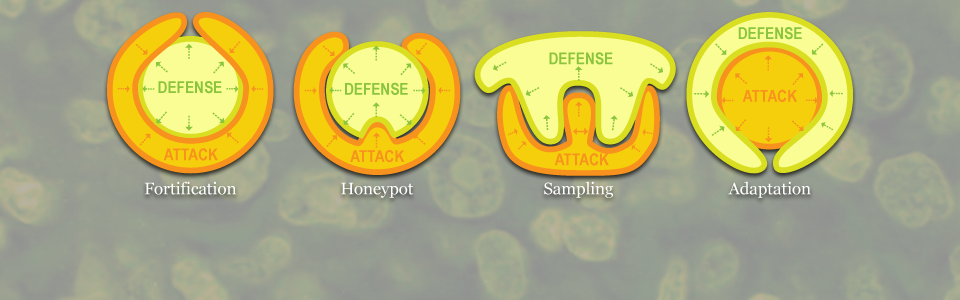
The reason (or at least one of the reasons) is, roughly speaking, that game theory assumes that the players follow the rules, whereas the cyber attackers often break the rules, and sometimes prefer to win that way. This type of adversarial situations brings with it new challenges. As an illustration, consider the toy model of a game of attack vectors, displayed in Figure 3. The first picture illustrates the slogan that the defenders have to defend all attack vectors, whereas the attackers only need to choose one. The remaining illustrations show how System turns this strategic disadvantage into an advantage by assigning increasingly greater weights to the information about the opponent. The final graphic depicts the strategic situation where the attackers have to conceal all identity markers, whereas the defenders only need to find one marker. Our adaptive immune system is a realization of this strategy. The illustrations thus show how the strategy of a ’fortress under siege’ on the left evolves into the strategy of a ’macrophage devouring a bacterium’ on the right. The illustrations correspond to the states arising in the mathematical model of this game.