Cyber space is the distance-free space of costless communication, where modern networking technologies assure that every two nodes appear to each other as neighbors. But since this ’end-to-end’ network service hides the communication routes, a pair of nodes with whom I am communicating cannot be distinguished by their positions in the cyber space, like they are distinguished in the physical space. And since I cannot tell these two nodes apart, the problem of authentication arises. In this way, cyber space challenges some of our basic communication assumptions. Similar authentication problems have, of course, already been treated in computer security. But cyber space also changes our notion of computation. In a computer, computation is the process of executing programs. In a networked computer, as a gateway into cyber space, computation ceases to be programmable in the old sense, as the processes invoke each other across the network, and run out of sight, beyond the horizon. Computation is therefore not fully and directly controlled by programs any more, but it can only be steered indirectly, through security protocols. Network computation is not a pure artifact of programming, but it involves natural information processing, like life, or society. Although it still involves a lot of programming and engineering, network computation as a natural process is thus not only a subject of engineering, which synthesizes artifacts, but also a subject of science, which analyzes natural processes. Cyber security requires that we take the ’science’ in ’computer science’ seriously.
Cyber Security Solutions and the Gap
As a new problem area of great economic, political and technical interest, cyber security has attracted a lot of attention, and focused efforts from the governments, from security industry, and from academia. Extensive and focused legislative and policy efforts have been undertaken in many countries, attempting to tackle the problems cutting across all areas of social life, from national security and governance, through industry, economy, to culture and social networking. The looming dangers of cyberwar and the intricacies of protecting the critical infrastructure from cyber attacks have been quickly recognized by the governments and their agencies. The grave economic losses to cyber attacks have been extensively analyzed, publicized, and transformed into significant business opportunities for security industry. The complex and quickly evolving problems of social networking in cyber space, such as cyber bullying and loss of privacy, have attracted a lot of public attention and interdisciplinary research. The gentle reader has probably already encountered much more information about all these problem areas than could fit into this article. Figure 1 illustrates the main cyber security problem areas, ranging from cyber war, through cyber crime, to cyber bullying. Figure 2 illustrates the main types of cyber security solutions.
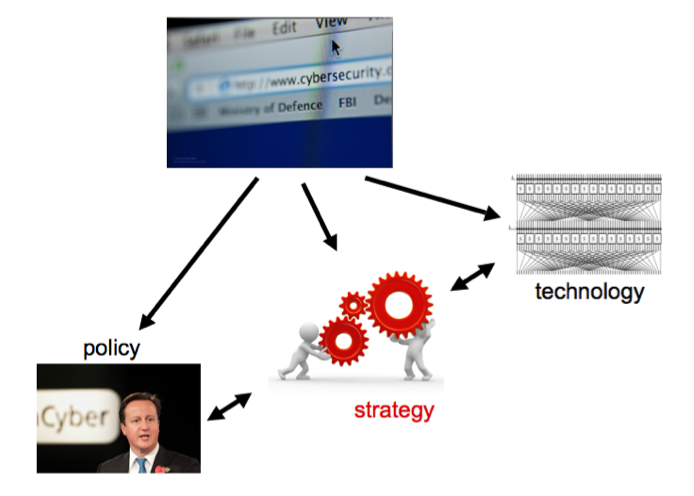
The two distinct families of approaches, at the two ends of the spectrum, tackle the cyber security problems through
- policy, i.e. the legislative and regulatory efforts of governments and industry consortia; and through
- technology, i.e. by adapting and extending the existing cryptographic techniques for cyber security applications.
To connect and coordinate the two types of solutions, the stakeholders from governments, industry and academia initiated broad collaborative networks, casting aside many old boundaries. In cyber space, no one can win without their friends, not the attackers, and not the defenders. The main challenges, however, remain on the middle ground, between the technical solutions and the policy solutions. The strategic gear box in the middle of Figure 2 is needed to synchronize the engine of cryptography with the wheels of policy. Although the interdisciplinary combinations of the methods from social and computational sciences provide some solutions, it seems unlikely that a toolkit for management of computational and economic resources will be obtained by mixing the existing toolkits. The genuinely new adversarial situations that arise in cyber space require genuinely new adaptive strategies, leading to security as equilibrium, through economics. This strategic middle ground, the gear box on Figure 2, is the area that we are studying at ASECOLab.